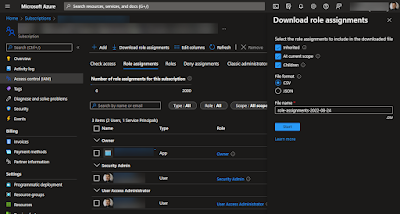
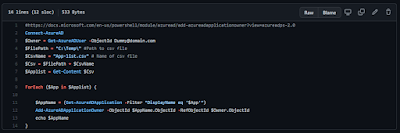
Removing all "Unknown" object from permission/access list in Azure (IAM)

I do not like to have permission in Azure that gives access to "Unknown". I consider this a "visual" disturbance, a documentation issue, and a potential security risk. So I usually delete them when I find them. You can find them by browsing around the entire portal manually or you can find them by using a script to document all access like my script explained in "Documenting Azure resources access (AIM)" To ease the cleanup process I created a script based on my findings from this blog . I basically extended it to go through all my subscriptions and document what it does during the process So it will go through all subscriptions (with some exceptions). Documents all findings in a CSV file, remove the unknowns and then documents what has been removed in a text file at the end. I Was not able to test the text file part, since I already had cleaned up everything when I figured out that documentation of what actually got removed was something that should be...