Documenting Azure resources access (AIM)
There are many situations when you want to know the access structure for all your Azure resources. Examples could be:
- Documentation
- Cleaning out permission given to individuals instead of groups
- Safe screening (groups/individuals that should not have access)
- Deleted identities still visible in the AIM list
- Preparing for features like Privileged identity management (PIM)
- Comparing changes in access since the last audit
- Etc
And the portal built in GUI works but is not particularly flexible or easy to use when you have multiple subscriptions
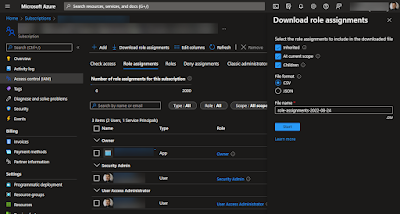
The Portal solution are just to go into "Subscriptions", select the subscription and "Access Control (AIM)
Here you can check a specific user or groups access, look at all role assignments or select the "Download role assignments" function at the top.
You can select to not include the inherited if you don't want to see permission given at the management or root level. And you can add the children option to get the resource groups and resources permissions as well
In my case, this was not enough so I got help from my colleague Gunnar to create a script to give me what I wanted.
I created two different scripts, the first one "DocumentSingleSubsAIM.ps1" that gives me a single csv file for the subscription (manually typed/replaced in the script)
The second script "DocumentAllSubsAIM.ps1", will automatically find all your subscriptions if you have multiple (excluding the ones mention in the script like the Azure AD and Visual Studio subscription). It creates a csv file for each subscription and one for all subscriptions combined.
It should be easy to add and adjust the results you want to add to the reports. My current result looks something like this:
The Empty name and "unknow" type indicate that there is a user/group/app that have been deleted.
You will find both script in my Github repo:
Scripts-For-Sharing/Azure/PIM/Azure resources at master · OTvedt/Scripts-For-Sharing (github.com)
Scripts-For-Sharing/Azure/PIM/Azure resources at master · OTvedt/Scripts-For-Sharing (github.com)